Encrypting Server Name Indication in TLS
A growing fraction of our webservers are now reachable via https instead of http. With the http scheme, all the information is transported in plain, including the HTTP headers, cookies, web pages and other sensitive information. For many years, https, which combines http with Transport Layer Security, has been restricted to sensitive web sites such as those that require a password or e-commerce. During the last five years, the deployment of https changed significantly. Today, Mozilla’s telemetry reports that roughly 80% of the webpages downloaded by firefox users are served over https.
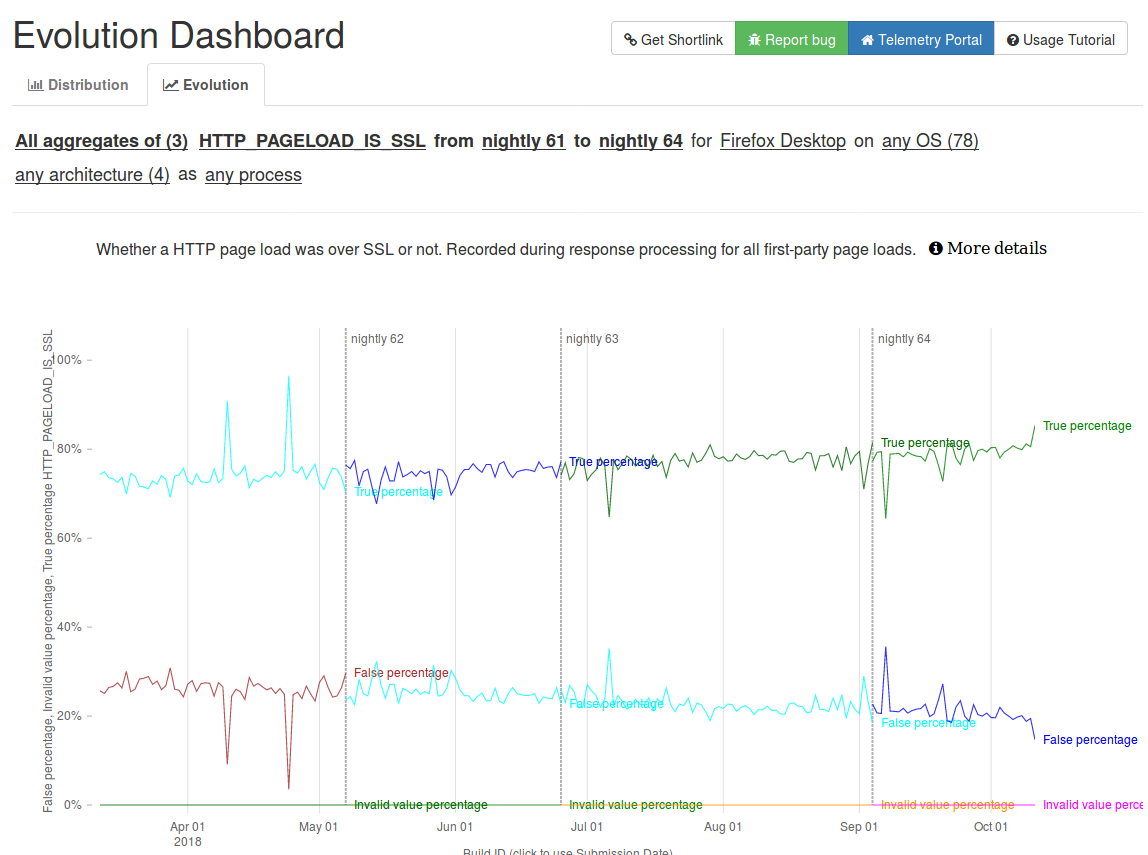
The utilisation of TLS improves a lot the privacy of web browsing compared to
plain http given that all information exchanged is both encrypted and authenticated. However, there are two important limitations to this. First, the IP address of the server remains visible. If the server that you visit is only reachable via one IP address, your ISP or anyone who manages the Wi-Fi network that you use can infer that you interact with this specific server. Nowadays, many large webservers are hosted by Content Distribution Networks. This implies that a small set of servers host a very large number of domain names. If someone tracks the destination address of your https connections, he cannot immediately know which site your are visiting. It could either be a gaming platform, a newspaper or even a government site. However, there is a caveat with TLS. Most browsers and web servers use a TLS extension that is called Server Name Indication. This extension was defined in Section 3 of RFC6066. It allows encoding in clear text the domain name of the server. On a server that hosts a single webserver, this information is redundant with the server’s IP address and domain names. However, on a CDN server, this information is important because its allows the server, which can support hundreds of servers or more, to determine the domain name (and the associated certificate) that needs to be used to handle this connection. This figure below illustrates such a Server Name Indication TLS extension in Wireshark.
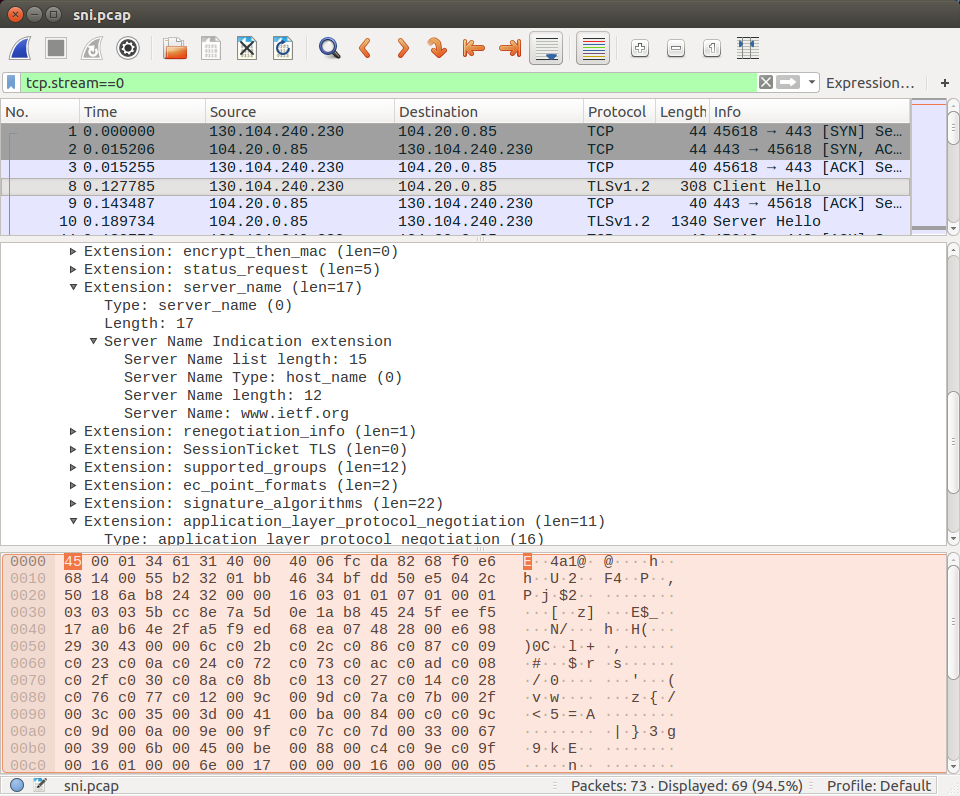
This Server Name Indication is useful for servers, but it is also widely used by firewalls, notably in enterprise networks, and content filtering middleboxes in some countries to block access to specific web sites. This dual-usage of the Server Name Indication has been discussed within the IETF and a new solution that allows encrypting this information has been accepted in draft-ietf-tls-sni-encryption-03. The encrypted SNI information is still valuable for the CDN servers but is does not leak privacy related information to firewalls and content filtering middleboxes.
The support for encrypted SNI has been implemented by at least Firefox and Cloudflare. Several recent blog posts describe their implementations are encourage users to test this new feature:
- https://blog.cloudflare.com/encrypted-sni/
- https://blog.cloudflare.com/esni/
- https://blog.mozilla.org/security/2018/10/18/encrypted-sni-comes-to-firefox-nightly/
- https://blog.cloudflare.com/encrypt-that-sni-firefox-edition/
This new TLS extension should improve the privacy of your web browsing, at least when you are interacting with large websites hosted on large CDN providers. If you visit a website that is identified by a single IP address or block of IP addresses, nothing really changes.
