Internet scanning, Latencies, Internet satellites make astronomers angry, Encrypted Client Hello canot be disabled on Chrome, New compression techniques, Cryptography 101, your Smart TV probably spies on you, round robin DNS, OVH failure
Internet scanning is the act of transmitting packets to remote hosts to determine whether they listen on specific protocols or ports. Researchers have used scanning to understand the deployment of new services on the Internet. Attackers have used scanning to detect vulnerable hosts which could be compromised. In the early 2000s, it was difficult to quickly scan the entire IPv4 addressing space. nmap made it simple for network administrators to detect servers in their network. Nowadays, with software such as zmap, anyone equipped with a 10 Gbps interface can quickly scan the entire IPv4 addressing space for various purposes. A recent article analyzes the evolution of scanning during the last decade. During this period, Internet scanning has increased 30-fold. Since 2020, the growth is not anymore exponential, but the scans are spread over the entire port range.
Networking students know that latency is a key performance characteristic in many networks. The https://cheat.sh/latencies website provides a nice visualization of the latencies that every CS student should know. Historical information is also available at https://colin-scott.github.io/personal_website/research/interactive_latency.html
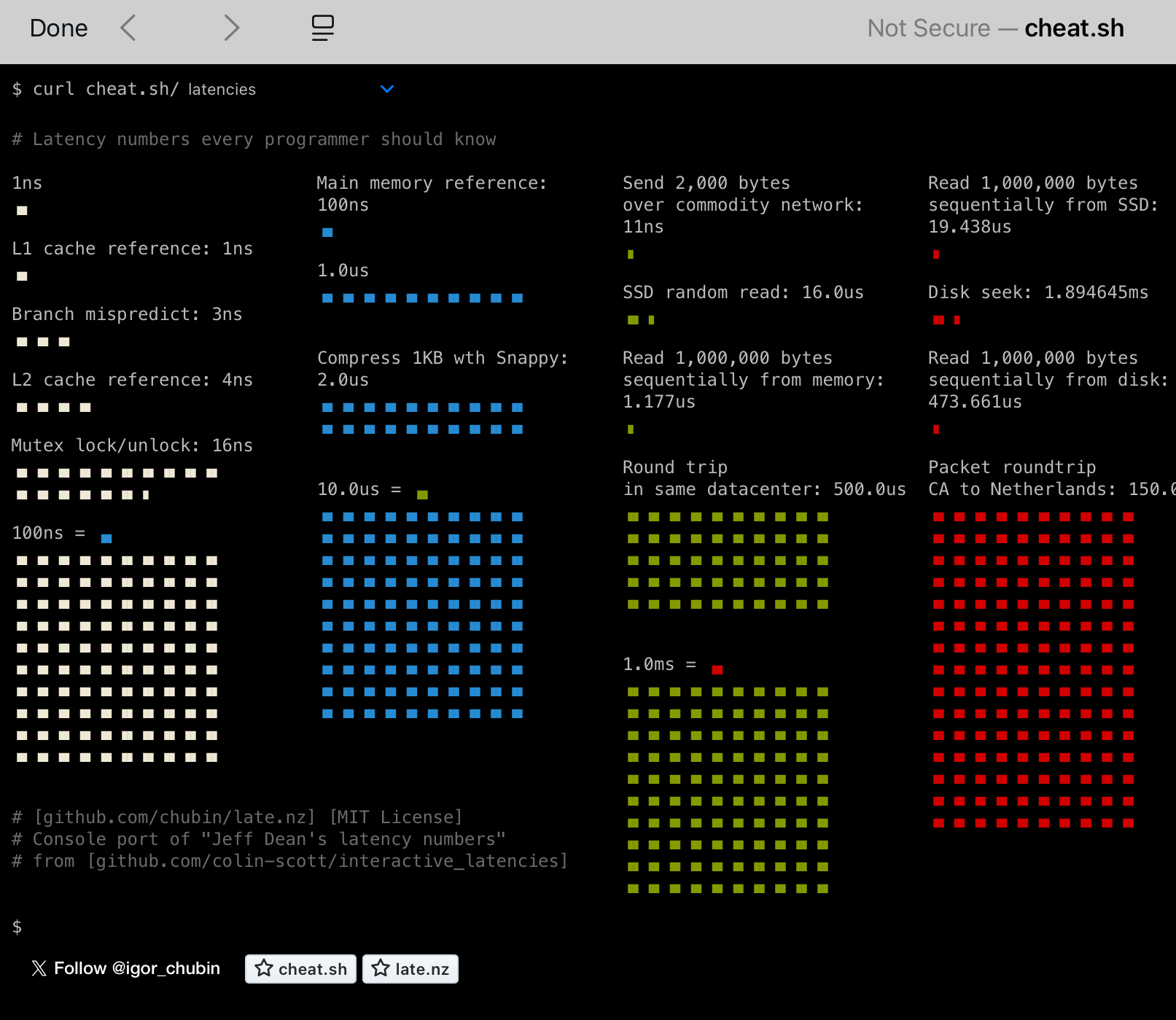 Source: cheat.sh
Source: cheat.sh
Low-orbit satellites such as Starlink, OneWeb, and other constellations provide Internet access services and other telecommunication services. These services can be useful to reach ships or serve areas with low population densities. However, satellite operators aim to serve many more users and deploy many satellites. Radio astronomers are worried by the interference caused by all these satellites. Their deployment could block the utilization of different types of radio telescopes.
In TLS 1.3, when a client opens a TLS session, it sends the name of the server in clear in the SNI field of the ClientHello. This field is used by servers and load balancers to determine which service is contacted by the client. Unfortunately, this information can be used to block access to some servers or track the websites visited by users. The IETF is finalizing a technique to encrypt the TLS Client Hello. Although the RFC has not yet been published, it has already been adopted and deployed. On the browser side, Google has recently announced that this feature is enabled by default on Chrome and that users will not be able to disable it. Enterprises using firewalls that rely on the SNI to filter Internet traffic might be disappointed by this move… On the server side, Cloudflare has also enabled the support for Encrypted Client Hello.
Various IETF protocols include compression techniques such as zlib or brotli. zstandard was published in 2021. Cloudflare reports some results with this new compression method in a blog post.
Smart devices enable many opportunities to collect more data about humans. A recent article analyzed smart televisions from Samsung and LG. These televisions implement a tracking approach called Automatic Content Recognition (ACR). In a nutshell, these televisions capture the image displayed on the TV screen regularly and compare it with a content library. A black-box audit of the ACR network traffic reveals that ACR continues to work if the user connects a PC to the television. The article analyzes the amount of data exchange but does not reveal the information sent by the televisions to the servers operated by Samsung and LG. If you thought your television was dumb… If you think that your smartphone is much safer from a privacy viewpoint, you will probably be worried by this blog post.
Alfred Menezes, one of the co-authors of the Handbook of Applied Cryptography, will retire in September 2025. One of his post-retirement projects is to develop free, online courses on applied cryptography. He has started to publish the video lectures of his Crypto 101 course.
Two letters, two-level domain names correspond to internationally recognized countries and territories. The “.us” prefix corresponds to the United States of America, “.tv” to the Polynesian island Tuvalu, and “.io” to the British Indian Ocean Territory. The UK has recently agreed to hand over the control of this territory to Mauritius. Eventually, ISO, which maintains the list of two-letters country codes, will probably remove the “.io” code. It is unlikely that the corresponding domains will disappear, as explained in this article.
An interesting blog post reveals the cost of 100 Gbps links across the Atlantic.
Ward Christensen, inventor of BBS and of the XMODEM protocol, passed away(https://arstechnica.com/gadgets/2024/10/ward-christensen-bbs-inventor-and-architect-of-our-online-age-dies-at-age-78/) at the age of 78.
The shortest path algorithm invented by Edsger Dijkstra in 1956. It is still a key element of the link-state routing protocols. A very interesting article written by Ben Brubaker for Quanta provides several interesting insights on this important algorithm.
Round-robin DNS is a technique that is used by nameservers to return answers for the same request for load balancing or resiliency purposes. An interesting blog post analyzes how different browsers interpret these responses.
A recent study reveals that, in the USA, most smartphones exchange data using Wi-Fi networks.
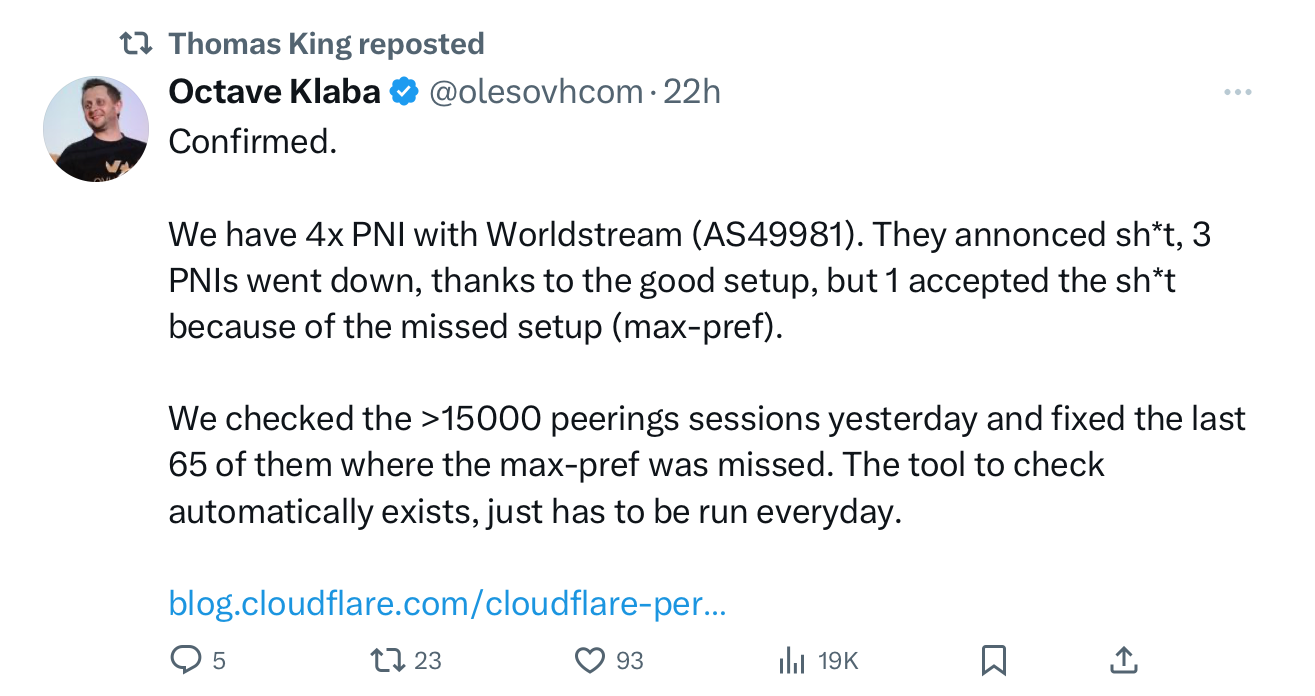
At the end of October, OVH, a French cloud provider, suffered from a routing problem. Cloudflare provides some information about the reasons for this outage. Shortly after, Octave Klaba, OVH’s founder and CEO, confirmed that the problem was caused by one of their upstreams, WorldStream, announcing too many prefixes.
The eBPF instruction set, which enables developers to insert code inside the Linux kernel, is now documented in RFC9669. Thanks to the eBPF virtual machine, the Linux kernel is more flexible and more extensible. This technique has also been proposed to extend Internet protocols.
This blog aims at encouraging students who read the open Computer Networking: Principles, Protocols and Practice ebook to explore new networking topics. You can follow this blog by subscribing to its RSS feed or by following @cnp3_ebook on mastodon. Feel free to share the posts that you find interesting on your preferred social network.
