Details matter in protocol security
Securing network protocols remains a difficult task as illustrated by the KNOB Attack that was recently announced on a wide range of Bluetooth devices. Bluetooth is a widely used short-range wireless technology that is used to connect devices such as keyboard, mouse, headphones to computers. It also used to directly exchange data between mobile devices such as smartphones. It is also possible to use a Bluetooth link to exchange IP packets. The development of Bluetooth started almost thirty years ago and the first devices appeared 20 years ago.
When they pair, Bluetooth devices use a special protocol to negotiate an encryption key that allows to secure the data that they exchange. This security feature is important for Bluetooth users since it ensures that nobody can eavesdrop the keys that a user presses on his keyboard when typing his password. Unfortunately, the base Bluetooth protocol contains a severe security flaw that was only discovered by Antonioli, Tippenhauer and Rasmussen. The Bluetooth protocol specification contains a special feature that enables two devices to negotiate the amount of entropy of the keys that will be used to secure the data transfer. Bluetooth devices typically use an entropy of 16 bytes. Unfortunately, the Bluetooth protocol allows a device a impose an entropy that is as small as one byte. This is illustrated in the figure below.
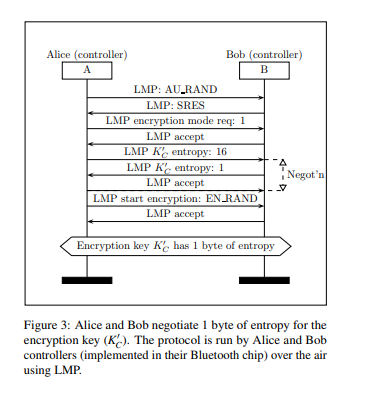
A one byte entropy is catastrophic for a security protocol. It implies that there are only 256 different values for the security key. Any attacker can easily brute-force such a key. The KNOB attack exploits this unused feature of Bluetooth. An attacker that sits in the middle between two communicating Bluetooth devices can intercept the packets that they exchange and force them to use a one byte entropy.
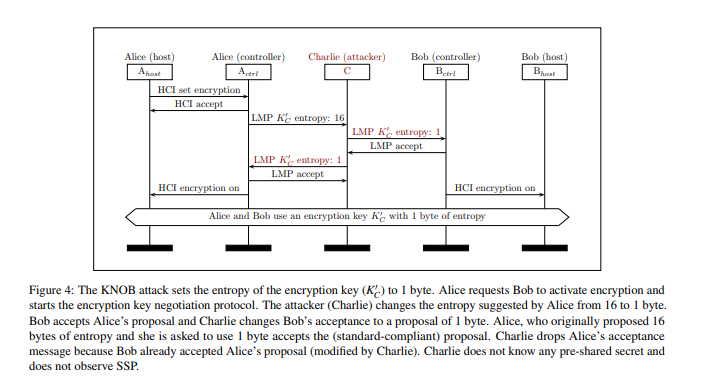
Unfortunately, almost all the Bluetooth devices and firmwares tested by the authors are affected by this flaw as mentioned in CVE-2019-9506.
For additional information, see :
D. Antonioli, N. Tippenhauer, K. Rasmussen, The KNOB is Broken: Exploiting Low Entropy in the Encryption Key Negotiation of Bluetooth BR/EDR, Usenix Security, August 2019
This blog post was written to inform the readers of Computer Networking: Principles, Protocols and Practice about the evolution of the field. You can subscribe to the Atom feed for this blog. These notes are also posted on the ebook’s Facebook page
