Memory safety, bloating web pages with JavaScript, future Internet eXchange Points, securing instant messaging and troubleshooting techniques
A large fraction of the client and servers that we used on the Internet are programmed using the C or C++ programming languages. These languages allow programmers to interact with the low-level hardware and achieve good performance. Unfortunately, small errors in the handling of memory have caused huge security problems. More recent programming languages like Rust provide stronger protection when accessing memory and allow to avoid a range of security problems. The White House has published a report that encourages the entire software industry to adopt techniques to design and implement memory safe programs.
Niki Tonsky looked in an interesting blog post at the size of the JavaScript code that different web pages load by default. Wikipedia only loads 200 KB of JavaScript, but other web pages can force you to load up to several tens of MBs of JavaScript only to access their front page. Even if many of these JavaScript codes are shared by different web sites, it is unclear why a single web page needs more code than entire programs and even operating systems several years ago.
Internet eXchange Points (IXPs) play an important role in today’s Internet by allowing many ISPs to peer efficiently at multiple locations. Thomas King, the CTO of DE-CIX, a German IXP, shares his reflections on the evolution of IXPs in the coming years. He envisions robots to automatically connect router cards, more automation, improved scalability, resilience and security and expects that more enterprises will use IXPs directly.
Many users rely on instant messaging to exchange information with friends, family and colleagues. These applications provide different levels of security.
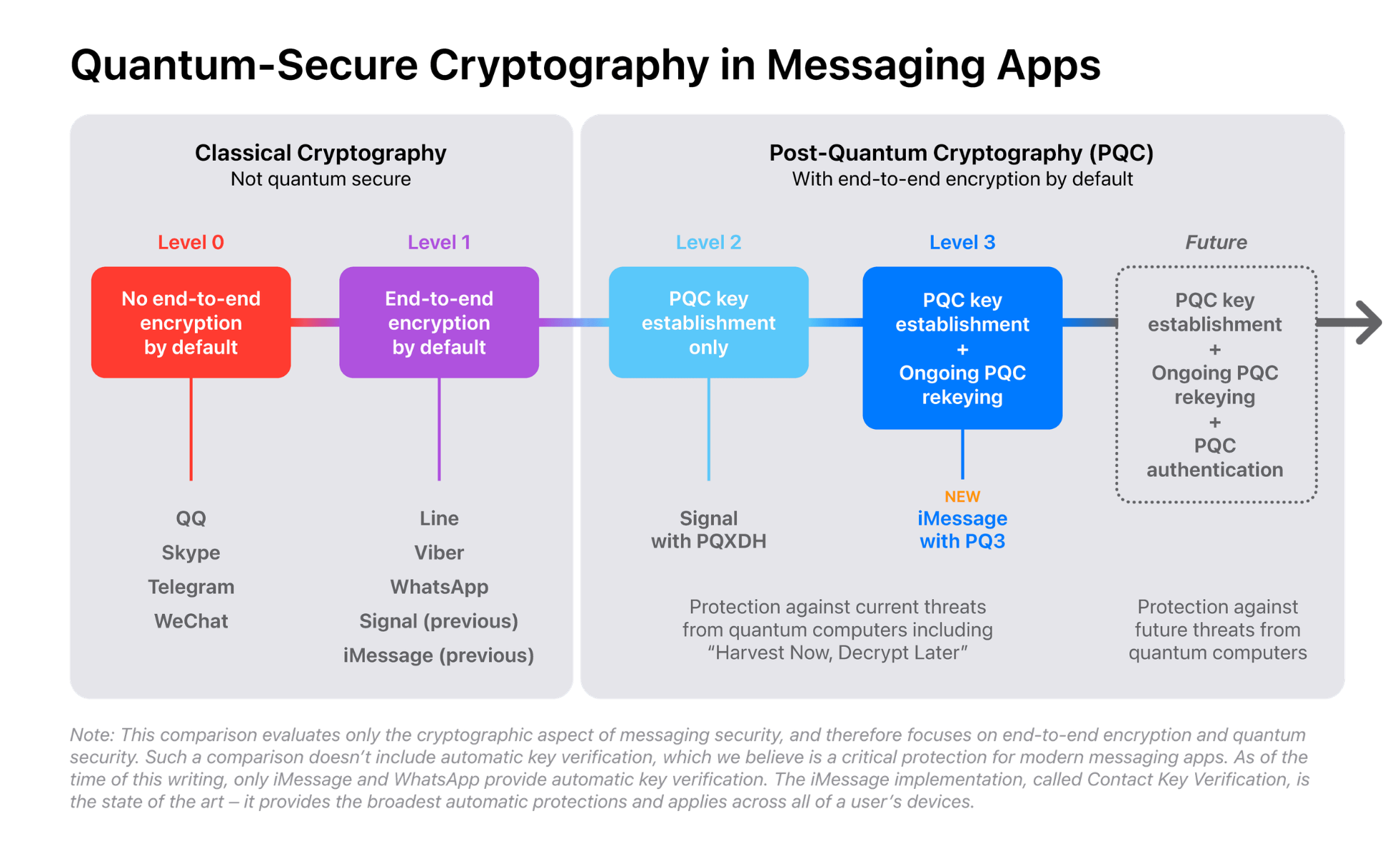
Apple has recently updated the cryptographic techniques used to ensure the security of the messages exchanged using iMessage. They provide a detailed overview of the new deployed technique in a blog post. The new technique allows to counter attackers that are able to collect encrypted messages, store them, possibly for several years, in the hope that new techniques such as quantum computers, will allow to decrypt these messages. The security of the new technique has been proven using formal methods, which is relatively rare in the Internet industry that usually focuses on shipping possibly unfinished products.
Network engineers often need to troubleshoot bizarre problems in the networks they manage. Like plumbers, they often improve their troubleshooting skills on the field by solving different types of problems. Students rarely manage real networks and it is difficult for them to acquire troubleshooting skills that are required by industry. Brandon Hitzel has collected a nice set of troubleshooting examples in a blog post.
This blog aims at encouraging students who read the open Computer Networking: Principles, Protocols and Practice ebook to explore new networking topics. You can follow this blog by subscribing to its RSS feed or by following @cnp3_ebook on mastodon. Feel free to share the posts that you find interesting on your preferred social network.
