DDoS attacks, X11, SMTP and co packet captures, rotating MAC addresses, CIDR
Distributed denial of service attacks were hundreds, thousands and sometimes millions of compromised devices send packets to target servers to overload them. When faced with such attacks, server administrators have limited solutions. They can subscribe to CDN providers like Akamai or Cloudflare that have enough server capacity to filter attacks while still preserving the availability of the content. A second option is to subscribe to scrubbing services from large ISPs that can also help to filter DDoS attacks. Besides that, there are no real options for NGOs and organizations willing to remain independent. A blog post argues for innovative solutions to its problem.
Forty years ago, Robert Scheifler announced the first version of the X Window System. This window system supported the remote display of bit mapped applications over a network. Thanks to X, user could execute a graphical application on a remote server and display it locally, even on simple clients.
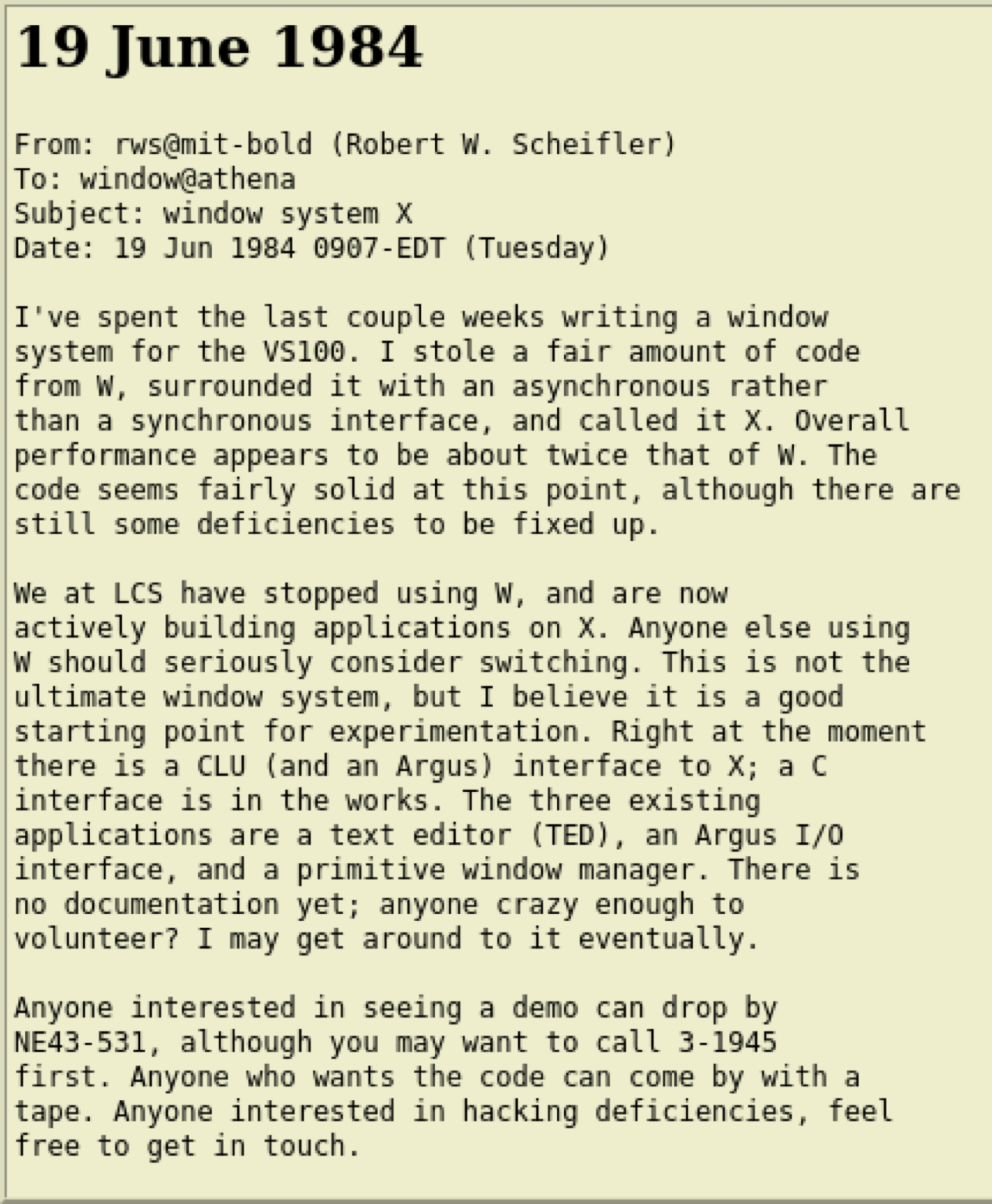 (source: https://www.talisman.org/x-debut.shtml)
(source: https://www.talisman.org/x-debut.shtml)
When learning new protocols, it is always interesting to analyzing traces with real packets with these protocols. Johannes Weber has released new traces with protocols such as SMTP, IMAP and POP using TLS.
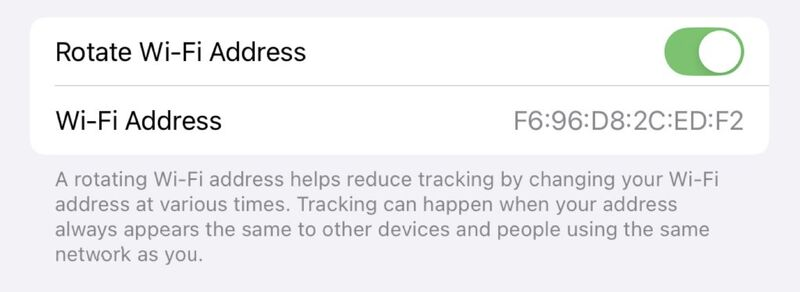
One of the basic design principle of local area networks was that each network interface has a unique address. This worked well for decades, until some companies started to track mobile devices using various techniques. If a possible device has a unique address that it uses every time it sends a packet in a local area network such as a Wi-Fi network, it becomes easy to recognize this device (and its user) every time it connects to the network. Initially, the IPv6 addresses included the MAC address in their low order bits, which made it possible to track devices from any where with their IPv6 address. The IETF proposed the privacy compliant IPv6 addresses. In parallel, device vendors started to use random MAC addresses. These devices typically use one random MAC address in a given Wi-Fi network and change of address when they move to another network based on its SSID. With the next version of iOS, apple has announced that they will go one step further by rotating MAC addresses. The MAC addresses of iPhones and iPads will regularly change. Keep this in mind if you have use or manage a network where MAC addresses need to be registered to obtain an IP address from a DHCP server…
IPv4 was initially deployed by assigning blocks of addresses to organizations. The largest received a class A or /8 subnet. Most universities were assigned a class B or /16 subnet. Smaller companies were allocated a class C or /24 subnet. This organization of the IPv4 addressing space was not optimal and resulted in a waste of IPv4 addresses since class A address blocks were too large for most organizations and class B blocks were too small for ISPs. The IETF proposed in 1993 the Classless Interdomain Routing (CIDR) address assignment strategy. Since then, address blocks are assigned based on the expected number of hosts in an organization.
Jan Schaumann wrote an interesting blog post that studies a lot of data about the allocation of IP address blocks. This blog post provides a lot of interesting information on the distribution of address blocks among countries, the transfers of address blocks, the sizes of the allocations, …
This blog aims at encouraging students who read the open Computer Networking: Principles, Protocols and Practice ebook to explore new networking topics. You can follow this blog by subscribing to its RSS feed or by following @cnp3_ebook on mastodon. Feel free to share the posts that you find interesting on your preferred social network.
