TCP connect in details, deploying 5G, packet fragmentation, security attacks and traffic engineering
When a TCP client creates a connection, it must select an unused source port. On Linux, this is part of the connect system call. In theory, finding an unused source port is simple. In practice, finding this source port quickly without iterating on all established TCP connections is not so simple. A recent Cloudflare blog post describes in detail how the Linux connect system call works.
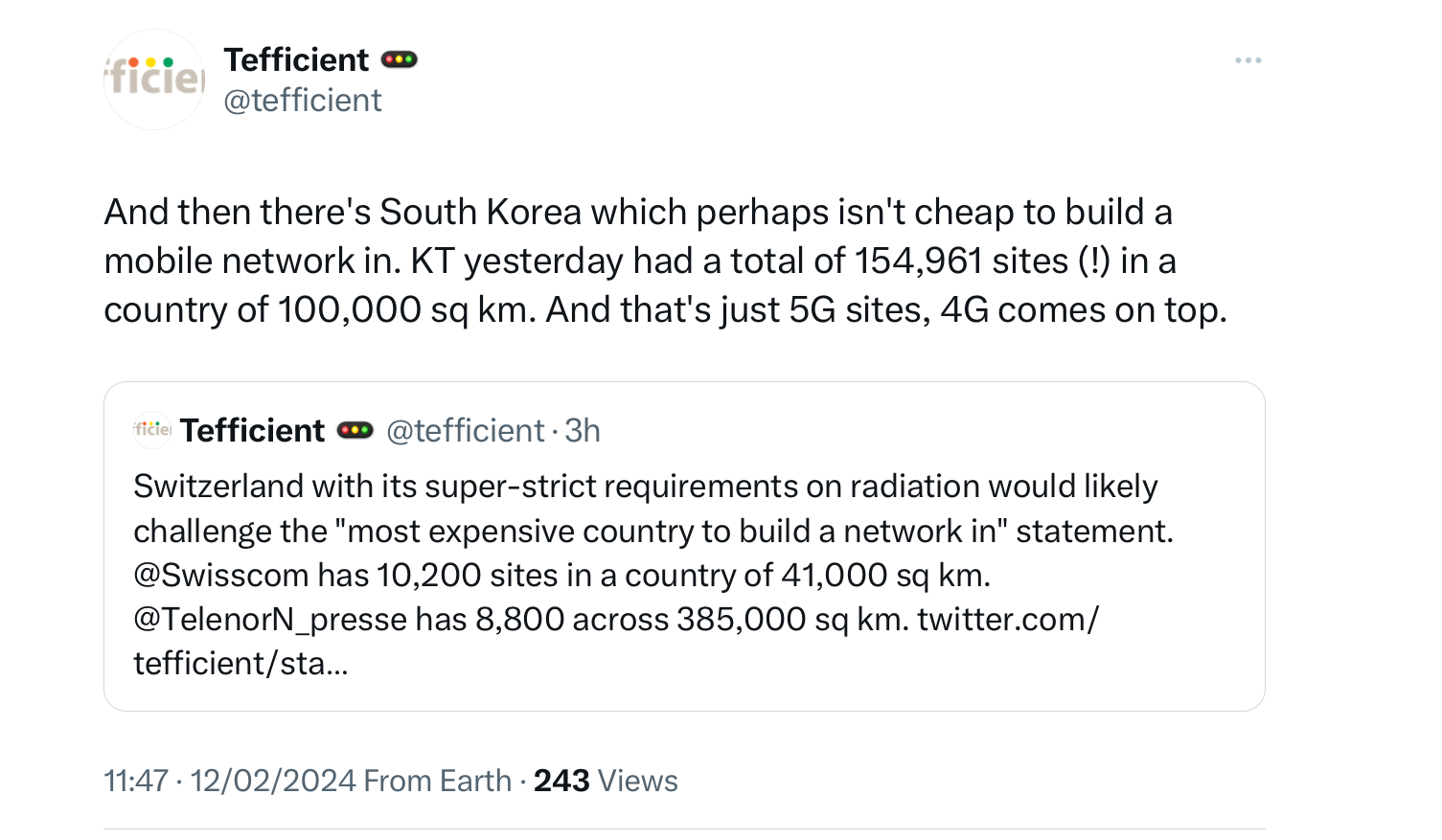
5G networks are being deployed in several countries. An interesting post on X by tefficient estimates the number of 5G sites in different countries and compares it with the surface of the country.
- 154,961 sites for KT in South Korea to cover 100,000 sq km
- 10,200 sites for Swisscom in Switzerland to cover 41,000 sq km
- 8,800 sites for Telenor in Norway to cover 385,000 sq km
In parallel with these terrestrial deployments of cellular networks, several companies are now exploring the possibility of using satellite to provide cellular services. The latest Starlink satellite is already capable of exchanging text over 4G/LTE connections as explained in a recent IEEE Spectrum article.
IPv4 and IPv6 use different strategies to support packet fragmentation and the networking stack can be configured in different ways using socket options whether or not to generate fragments. Valerie Aurora developed fragquiz, a software tool running on Linux and MacOS that allows you to generate different types of fragmented packets and also test your knowledge of packet fragmentation.
Large platforms are also targets for attackers. Most of these attacks are only discussed within the companies that manage these platforms and sometimes with the government, but there are a few exceptions. Cloudflare published a blog post describing in detail an attempt to attack a part of their platform. The interesting point about such blog posts is that they often reveal interesting information about the operation of the affected services.
Internet Service Providers use a variety of traffic engineering techniques to control the packets that flow through their networks. Many of these techniques work by tuning various IETF protocols and their implementations on routers. RFC9522 provides a detailed survey about modern traffic engineering techniques. A good starting point to explore this domain.
This blog aims at encouraging students who read the open Computer Networking: Principles, Protocols and Practice ebook to explore new networking topics. You can follow this blog by subscribing to its RSS feed or by following @cnp3_ebook on mastodon. Feel free to share the posts that you find interesting on your preferred social network.
